thick client application penetration testing github|owasp thick client top 10 : export Test For Run Time Manipulation. Try to analyze the dump file; Check for process replacement; Check for modifying assembly in the memory; Try to debug the application; Try to identify dangerous functions; Use breakpoints to test . Resultado da Clay Jensen. Christian Navarro. Tony Padilla. Alisha Boe. Jessica Davis. Amy Hargreaves. Mrs. Jensen. Brandon Flynn. Justin Foley. Newcomer Katherine Langford plays the role of Hannah, a young.
{plog:ftitle_list}
Pokemon Showdown has released beta formats for the eighth generation of Pokemon! You can now battle in Gen 8 Random Battles, OU, Doubles OU, and Balanced Hackmons! More formats will be released as the beta progresses.
Identifying and exploiting vulnerabilities within the thick client application itself, such as insecure configurations, input validation flaws, or logic errors, is crucial in penetration testing.Test For Run Time Manipulation. Try to analyze the dump file; Check for .
Vulnerable Client-Server Application (VuCSA) is made for learning how to .Vulnerable Windows Application for Pentesters from the house of DarkRelay .Test For Run Time Manipulation. Try to analyze the dump file; Check for process replacement; Check for modifying assembly in the memory; Try to debug the application; Try to identify dangerous functions; Use breakpoints to test . Vulnerable Client-Server Application (VuCSA) is made for learning how to perform penetration tests of non-http thick clients. It is written in Java (with JavaFX graphical user interface) and contains multiple challenges .
web penetration testing checklist
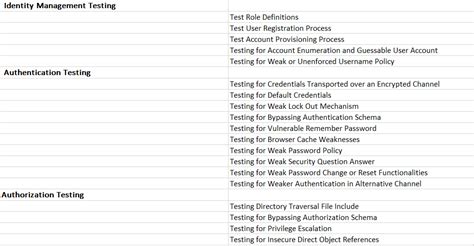
Introduction to Pentesting Thick Clients Applications. Checklist for Pentesting Thick client applications. General index of the course. Introduction. Tools for pentesting thick client applications. Basic lab setup. . NETWORK TESTING. **Test For Network**. - [ ] Check for sensitive data in transit. - [ ] Try to bypass firewall rules. - [ ] Try to manipulate network traffic. **Tools Used**. - . In this blog, we presented our thick client pentest methodology and common attack vectors, including tools that can be used during penetration test engagements. The main focus areas were derived from the OWASP .
ultimate tensile strength testing machine
Labs: DVTA — Vulnerable Thick Client Application. https://github.com/secvulture/dvta — Our testing Vulnerable application/Environment for few test cases. Thick client applications can be . We will make use of the DVTA 2.0 (https://github.com/srini0x00/dvta) application for capturing the traffic. Setting up details of DVTA lab environment may be out of scope for this article.Vulnerable Windows Application for Pentesters from the house of DarkRelay Security Labs. The project is along the lines of DVWA, AWSGoat and other similar projects, to help the cybersecurity community practise their skills in .Using the applications own proxy settings (if available) A good first step is to check if the application itself supports proxy. If it does, and it communicates over HTTPS you can proxy .
thick client pentest checklist
Resources for Application Security including , API, Android, iOS and Thick Client Topics android security hacking cybersecurity penetration-testing infosec application-security pentesting bugbounty appsec security-testing .Purpose of the application is to educate students on Windows thick client penetration testing. If you use this application for malicious means or if your server is compromised via an installation of this application, DarkRelay does .You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window.
Damn Vulnerable Thick Client App. Contribute to secvulture/dvta development by creating an account on GitHub. Damn Vulnerable Thick Client App. Contribute to secvulture/dvta development by creating an account on GitHub. . DVTA is a Vulnerable Thick Client Application developed in C# .NET. Some of the vulnerabilities covered in this . Application Security: Assess and secure web applications for vulnerabilities. 2: API Security: Test and enhance the security of APIs and microservices. 3: Mobile Application Security: Evaluate the security of mobile apps and devices. 4: Thick Client Application Security: Assess thick client applications for security issues. 5: Source Code .
After finishing the 1st shot, open DVTA application and login using the regular user credentials and explore the application. Now, click on 2nd shot and wait until it finished. Then, click on Compare, in order to compare two captured registry shots .Purpose of the application is to educate students on Windows Thick Client Pentesting. If you use this application for malicious means or if your server is compromised via an installation of this application,DarkRelay does not hold any responsibility!
Proxy-Aware Thick Client: If Thick Client application has a built-in feature to set up a proxy server, then it is known as a proxy-aware Thick Client. Brp Suite (Burp's Invisible Proxy Settings to Test a Non-Proxy-Aware Thick Client Application): Go to Request handling in the Proxy listener window, fill in the appropriate host and port .
The security analysis on the thick client application is always exciting because of its complexity, varying kind of architecture and protocols used to communicate with the external systems.
A collection of awesome penetration testing resources, tools and other shiny things - enaqx/awesome-pentest . TrevorC2 - Client/server tool for masking command and control and data exfiltration through a normally browsable website, . autochrome - Chrome browser profile preconfigured with appropriate settings needed for web application testing.
Enhance your cyber security with RBT Security's application penetration testing assessments, covering web, mobile, APIs, Thick Client penetration testing. . Thick Client penetration testing. Skip to content. Services Close Services Open Services . Cloud Penetration Test. AWS Penetration Test; Azure Penetration Test . Linkedin Twitter Github .Open Echo Mirage and DVTA application and login with creds.; In Echo Mirage go to Options > Configuration and select these rules in below image.; Next go to Rules > New > Direction = Any > Port = 21 > Intercept.; So we have got our rules which are intercepting the traffic of inbound and outbound traffic on port 21. Now go to Process > Inject > Select DVTA.exe.This repository lists TOP 10 vulnerabilities found during Thick Client Application penetration testing. Thick client application penetration is one of the gray area where-in lots of articles are available to test for the vulnerabilties but no proper guideline is available to lookup for. After performing penetration testing for large set of . More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects. . Android, iOS and Thick Client. android security hacking cybersecurity penetration-testing infosec application-security pentesting bugbounty appsec security-testing penetration-testing . real life penetration testing and learning by .
what machine is used for tensile testing
Anof-cyber/Application-Security More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects. . penetration testing and offensive security. security powershell hacking activedirectory penetration-testing infosec . security guide best-practices hacking owasp penetration-testing application-security pentesting bugbounty appsec .
10.7. Test Defenses Against Application Misuse 10.8. Test Upload of Unexpected File Types 10.9. Test Upload of Malicious Files 10.10. Test Payment functionality 11.Client-side Testing 11.Client-side Testing 11.1. .
Introduction to Hacking Thick Clients is a series of blog posts that will outline many of the tools and methodologies used when performing thick client security assessments. In conjunction with these posts, NetSPI has released two vulnerable thick clients: BetaFast, a premier Betamax movie rental service, and Beta Bank, a premier finance .When testing is completed, stop the containers using Ctrl - C and then type docker-compose down. Note - by default, the web server is available on 127.0.0.1:8080. Therefore, if testing with docker on the same machine as the BetaFast client, .Quick script to automate some basic tasks done during a OSX Thick Client or Software Penetration Test. Checks for things like ARC, PIE, Canary, Codesignature Flags, NSFileProtect, Signature and more. - GainSec/Mac-OSX-Application-Fingerprint-And-Security-Tool
thick client penetration testing methodology
DarkRelay's Windows application is an intentionally vulnerable application designed and developed to teach pen testers about thick client penetration testing. It is recommended to install this vulnerable application on an isolated virtual machine.A repository containing public penetration test reports published by consulting firms and academic security groups. Maintained by Julio @ Blaze Information Security (https://www.blazeinfosec.com)
Why thick client penetration testing? Thick client applications are not new having been in existence for a long time, however if given to perform a pentest on thick clients, it is not as simple as a Application Pentest. Thick clients are majorly used across organizations for their internal operations.PETEP (PEnetration TEsting Proxy) is an open-source Java application for traffic analysis & modification using TCP/UDP proxies. PETEP is a useful tool for performing penetration tests of applications with various application protocols. ⚡ - Warxim/petep Conclusion. This blog highlights different tools and approaches for testing a thick client application for vulnerabilities. The tools have remained the same over a period of time and there are no major changes in the way thick client applications have been assessed when compared to web / mobile applications, where introduction of new frameworks / technologies .
100kn tensile strength testing machine
Each SAP instance (or SID) is composed of three layers: database, application and presentation), each landscape usually consists of four instances: dev, test, QA and production. Each of the layers can be exploited to some extent, but most effect can be gained by attacking the database. Each SAP instance is divided into clients.You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window.
30 kn tensile testing machine
Comproveu les traduccions de Passa-tempo a català. Consulteu exemples de traducció de Passa-tempo en frases, escolteu-ne la pronunciació i aprengueu gramàtica.
thick client application penetration testing github|owasp thick client top 10